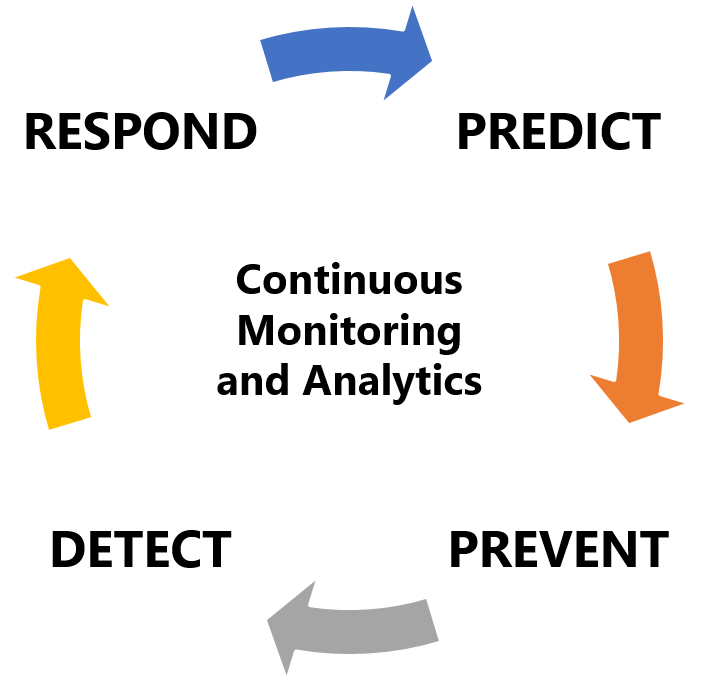
Cybersecurity Strategy

Going beyond a simple vulnerability scan, every organization needs to have a long-term vision and strategy when it comes to IT Security.
In-depth Security Assessments
Our Security Assessments are designed to ensure compliance with documented procedures and standards, and helps in equipping the customer to achieve industry best practices, while also determining and improving the security posture of your organization. We focus on the people and processes used to design, implement and manage security within your organization.
Even though it is IT management that usually initiates these Security Assessments, in performing them we make sure that there is a baseline involved for processes and policies within the entire organization.
The process includes:
Manual assessments
reviewing application and OS access controls
analyzing physical access to the systems
Automatic assessments
monitoring and reporting changes in the infrastructure
Make sure your business is safe and secured
IT Risk Assessment & Risk Management
IT Risk is the business risk associated with the use, ownership, operation, involvement, influence and adoption of IT within an enterprise or organization, and it is essential to company strategy, operations, financial reporting and compliance.
Almost every business decision requires executives and managers to balance risk and reward, and efficiency in that process is essential to an enterprise’s success. Too often though, IT risk (business risk related to the use of IT) is overlooked.
While other business risks such as market, credit and operational risks have long been incorporated into the decision-making processes, IT Risk has usually been relegated to technical specialists outside the boardroom, despite falling under the same risk category as other business risks: failure to achieve strategic objectives.

Address business risks related to the use of IT
Clarify and implement
Risk Governance (Appetite and Tolerance)
Evaluation and Response
Looking at IT Risk Management as a continuous process instead of a one-time fix.
Penetration Testing
Protecting customer privacy and preserving intellectual property presents a real challenge to every organization. Weaknesses can be exploited to retrieve secrets or even to be reverse engineered.
Our Penetration Testing services extend the Vulnerability Assessments, through testing the organization’s security by simulating the actions of an attacker and its potential consequences.
This helps organizations determine various levels of vulnerabilities and to what extent an attacker can damage the network, before that damage actually occurs, while also revealing security weaknesses that a typical vulnerability scan misses. It can even help in disaster recovery and business continuity planning.
Social Engineering Consulting
Even though it is rarely considered and addressed as an integral part of information security (and often simply ignored altogether), Social Engineering can still pose a great risk. Our Social Engineering consulting and assessment services allow you to detect weaknesses to better address your staff-related security issues. At times, IT Risk associated with the human factor can prove to be even more damaging than a technical issue, but many companies fail to acknowledge this fact.
The result of making use of our services is a more secure working environment against data compromising attempts, fraud, as well as a more threat-aware staff, increasing the overall security posture of your organization, be it through an actual assessment or just through staff awareness training programs.